North Korea: Putin's Ally in Cyberspace?
The alliance between North Korea and Russia provides a pretty grim proposal for the future of cyber and hybrid warfare.
Before I get started, let me be clear, as of the time that this article outline was drafted, there has been no confirmation of any North Korean cyber assets directly engaging Ukrainian targets since Russia’s full-scale invasion of Ukraine in February 2022. That said, things in cyberspace are almost never as clear-cut as they can be in the kinetic realm.
We all probably know at this point that North Korea (DPRK) has boots on the ground in Russia. 10,000 North Korean soldiers are, at the very least, in Russia’s Kursk Oblast, while the war continues to grind on with heavy casualties.
The ties between both countries seem to be growing. This is despite a wave of speculation that Russia’s economic situation and the sustainability of the war may make Putin’s prospects a bad bet for the North Korean regime.
I’m not going to pretend that I understand everything about the move. Russia still has a lot that it could offer the DPRK regarding resources, defense tech, and, maybe most important to Korea-watchers: nuclear weapons know-how.
But that’s not at the heart of where I wanted to go with this piece. Call it speculation, fear-mongering, or a thought experiment, I wanted to explore the following points:
Russia has a rich hacktivist ecosystem, and several threat actors typically working on behalf of Russian national interests have assessed that the DPRK’s Southern rival is now a viable target.
North Korea has an extremely capable cyber operations network that operates in criminal, espionage, and military capacities against targets all over the world. Have any of these behaviors escalated or changed since Putin’s June visit to Pyongyang?
Are there any hypothetical scenarios wherein collaboration between DRPK and Russian threat actors would be logical?
Is there any evidence of previous collaboration between Russia and the DPRK in cyberspace?
What could this all mean for Ukraine? Ukraine’s own cyber and information warfare infrastructure has become extremely capable and “battle”-tested since the initial Russian aggression in 2014.
How could this change cyber and hyrbid warfare?
A Brief Look At Lazarus
North Korea’s cyber program Bureau 121 exists in a space that readily accepts the blurring of espionage, financial theft, and cyber warfare activities. It is spearheaded and often blanket-referred-to by the infamous moniker, “Lazarus Group”, which has effectively become an industry catchall for “any North Korean cyber activity”. Some other current aliases, groups, and subgroups that are associated with 121/Lazarus’ activities include: Andariel, Bluenoroff, Sapphire Sleet, and UNC2970 (suspected but unconfirmed).
Established under the DPRK’s Reconnaissance General Bureau (RGB), 121 operates with the goals of circumventing sanctions and furthering state power. Despite limited internet infrastructure, North Korea has cultivated a formidable cadre of cyber operators, estimated at over 7,000 service members, drawn from elite technical institutions and trained under stringent state control.
Lazarus’ operations have evolved from attacks like 2009’s Operation Troy botnet (targeting South Korea’s government) to global campaigns such as the 2017 WannaCry ransomware attack. Financial theft is a hallmark, exemplified by the 2016 Bangladesh Bank Heist, where $81 million was siphoned through SWIFT banking systems, and more recently, massive cryptocurrency thefts, netting billions to fund North Korea’s nuclear ambitions.
[A botnet is a network of compromised devices—such as computers, IoT devices, or servers—that are controlled by a threat actor to perform coordinated malicious activities. These devices, often infected without the owner’s knowledge, can be used to amplify attacks like distributed denial-of-service (DDoS), send spam, or carry out further infections. Botnets can remain dormant and be activated for future attacks, as long as they evade detection and remediation.]
Unique among state actors, North Korea explicitly incorporates theft into its cyber strategy. With cyber-crime generating an estimated 8% of its GDP, the nation uses stolen cryptocurrency to evade sanctions and finance clandestine activities. Operating with impunity, often behind Chinese networks, these cyber campaigns actually demonstrate that the DPRK’s isolation can be leveraged as a strength, rather than a disadvantage, when exploiting adversaries’ vulnerabilities. After all, no matter what other nations say, no North Korean hacker will ever be extradited, as there’s no pretense of cooperation.
Lazarus Group represents a completely unique combination of statecraft and cyber-crime, undermining adversaries while enriching a heavily sanctioned regime. Given the context in which Russia finds itself, there might actually be a lot that it could learn from North Korea, despite Russia’s own advanced cyber capabilities.
Recent DPRK Cyber Activity
The DPRK has escalated its global cyber activities since doubling down on its support of Russia. This has been carried out with increasingly sophisticated tactics to target critical industries, financial institutions, and geopolitical rivals.
Here are some of the most notable examples in the past several months:
July: The US DoJ accused Andariel of using ransomware proceeds to fund theft of sensitive information from defense and technology organizations worldwide, including U.S. government agencies.
[Ransomware refers to a type of cyber attack wherein a victim’s computer has all or a significant portion of its contents encrypted, and cannot decrypt it without paying the threat actor for the decryption key.]
August: Microsoft discovered remote access vulnerabilities in its infrastructure that it attributed to North Korean threat actors.
[Remote Access is the ability of a threat actor to run commands or various programs on a targeted device, remotely.]
September: The FBI issued a warning about North Korean state-sponsored cyber actors heightening their social engineering campaigns against employees in the decentralized finance and cryptocurrency sectors.
October: Evidence was discovered indicating that state-backed actors from North Korea were collaborating with Play Ransomware, who are suspected to be Russian in origin.
November: SentinelLabs identified a new network of websites being utilized as a front for a fake IT workers’ scheme, operated by North Korea.
Their current tactic of choice is to use AI-generated profiles on recruitment sites such as LinkedIn to impersonate recruiters and venture capitalists. These attack vectors were pivotal in recent cryptocurrency heists, by either positioning threat actors in ways that they could install malware-laden tools, or even funneling job earnings into North Korea's heavily sanctioned economy, supporting its nuclear and ballistic missile programs. A critical aspect of this social engineering tactic is that, even if an impersonator isn’t hired, the hiring process may provide them with enough insider information to better formulate an attack.

Energy and aerospace sectors remain key targets for additional espionage campaigns. UNC2970 was recently discovered using job-themed phishing lures to deploy novel malware against tech companies in the US, UK, Netherlands, Germany, Sweden, Singapore, and others.
Pyongyang's strategy here is pretty clear: use cyber operations for both financial gain and intelligence gathering. Something that brings North Korea and Russia together in these ventures is that neither state is against working with criminal elements in cyberspace. There’s certainly no lack of such threat actors in Russia, and several are currently engaged against Ukraine.
Aligning Actors
Ransomware
Another recent development is confirmation of collaboration between state-sponsored North Korean groups and ransomware threat actors. The partnership between North Korea's Andariel Group and the Play Ransomware mentioned above exemplifies this, and is considered by Palo Alto Networks’ Unit 42 researchers to be the first documented incident of its kind.
In the report’s findings, it’s suspected that Andariel’s relationship with Play was that of the “initial access broker”—the entity able to find a way into the target network or device, and then sells or provides access to the ransomware group. Partnering with a ransomware group in this way allows Andariel to cause greater disruption at the conclusion of their operations, and an increased ability to cover their tracks.
“Hacktivism”
In response to confirmed reports of North Korean deployment in Kursk, the South Korean government publicly announced that they would consider sending lethal aid to Ukraine, a line that they had not yet crossed (and have since backed away from).
Russia has its own ecosystem of “hacktivists” and performative DDoS threat actors who often conduct these sorts of nuisance-level attacks in conjunction with Putin’s political and strategic goals.
[A Distributed Denial-of-Service (DDoS) attack is the most common cyber attack, wherein a threat actor overwhelms a target system, server, or network with an excessive amount of traffic or requests from multiple sources. This flood of traffic exhausts the target’s resources, rendering it slow or entirely inaccessible to legitimate users. DDoS attacks are often launched using botnets to amplify their scale and impact.]
One of the most infamous, and arguably competent of these lower-tier cyber auxiliaries is NoName057(16), who formed within weeks of Russia’s invasion, and have targeted entities within NATO and other perceived Ukrainian allies ever since.
On November 4th, about a week after it was confirmed that there were North Korean troops in Russia, NoName057(16) began launching a huge volley of DDoS attacks against South Korea (RoK). This was allegedly in response to statements by RoK leadership musing with enhancing its aid to Ukraine in light of the North’s involvement.
From November 4th until November 10th, NoName057(16) claimed to have caused at least 75 disruptions to essential services, including public transit, police departments, and various government ministries and political parties:
Russia—while not having quite as explicit of a relationship with its home-grown threat actors as the DPRK demonstrated with Play Ransomware—has been proven to maintain a long-standing relationship with cyber-criminals. Reports over the past two decades have asserted that the Russian government will tolerate groups who choose targets that align with their geopolitical goals.
A famous example of this is Russia’s alleged accommodation of Lockbit 3.0, an iteration of a massive ransomware gang that, until 2024, was among the most accomplished in the world. The group’s expected revenue is in the hundreds of millions from its numerous extortion payments.
Another similar threat actor that has credible connections to the Russian government is Evil Corp, which has more specifically targeted large financial institutions, and has had a financial impact also estimated to be in the hundreds of millions. A 2020 joint investigation by Bellingcat, Der Spiegel, and The Insider indicated that Evil Corp has a direct connection to Russia’s Federal Security Service (FSB).
Can North Korea “Hack It”?
While I wouldn’t think a punch-for-cyber-punch conflict between Ukraine and North Korea is imminent, even in the scenario I’m implying, it’s worth taking stock of how Ukraine has conducted its defense since Russia made its expansionist moves in 2014.
Ukraine has had to step up its capabilities in response to persistent cyber attacks from Russian threat actors in that time. Since the annexation of Crimea, groups connected to Russian intelligence services intensified their digital sabotage in sectors including government, energy, and finance.
Petya/NotPetya - 2017
In June 2017, Ukraine experienced a significant cyberattack involving a modified variant of the Petya ransomware, dubbed “NotPetya”. This malware rapidly spread to government agencies, financial institutions, and critical infrastructure, causing widespread disruption. The attack incapacitated systems at the Chernobyl nuclear plant, forcing a switch to manual radiation monitoring.
Unlike typical ransomware, NotPetya's primary function was destructive; it irreversibly encrypted data without providing a viable decryption method, indicating its intent to cause maximum disruption rather than extort ransom payments. The initial infection vector was traced to a compromised update in the Ukrainian accounting software, M.E.Doc, which facilitated the malware's rapid dissemination within Ukrainian networks.
The attack was attributed to Sandworm, a group positively identified as a part of Russia’s military intelligence apparatus.
Since 2022
As the full-scale invasion commenced, the cyber-attacks only intensified, particularly against internet and energy resources. Investigations by Mandiant showed that Russia is experimenting with hybrid tactics utilizing cyber attacks against critical infrastructure, alongside conventional weapons, in order to improve their efficacy.
Ukraine’s Adaptations
In response to these threats, Ukraine’s government established dedicated cybersecurity units and collaborated with international partners to enhance resilience. The European Union, for instance, launched the EU–Ukraine cyber-dialogue in June 2021 to support Ukraine in countering cyber-attacks.
The ongoing conflict has also seen the emergence of volunteer cyber initiatives, such as Ukraine's "IT Army," which conducts cyber operations against adversarial targets. This group, comprising thousands of volunteers, has been involved in various cyber activities aimed at disrupting enemy operations. It also can’t be understated that, prior to the invasion, Ukraine had a massive talent pool of IT workers that could easily be activated for such operations.
This has effectively resulted in Ukraine becoming another nation, not unlike North Korea, that is far more powerful in the cyber domain than its perceived international standing would suggest. For both Russia and North Korea, it is no easy target.
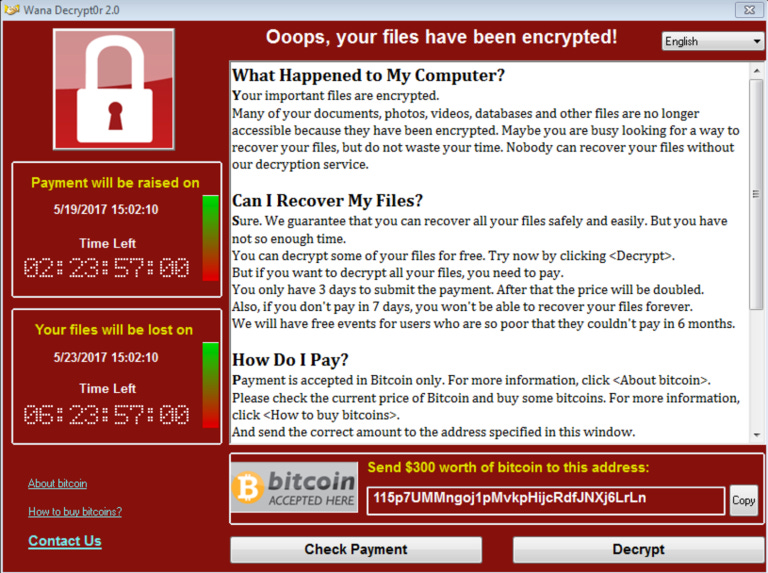
North Korean Innovation, WannaCry - 2017
While NotPetya took much of the world’s attention in the summer of 2017, it actually proceeded another massive ransomware incident that has been attributed to Lazarus Group: WannaCry. While a distinct project, sponsored by a different State, WannaCry was developed utilizing a complex stack of exploits and tools similar to those of Petya/NotPetya. Both were built utilizing the EternalBlue exploit, a cyber-weapon stolen and leaked from the US National Security Agency.
In a matter of days, it had spread to over 200,000 devices in 150 countries, which included thousands of devices in Ukraine.
It could be argued that Russia was taking from North Korea’s playbook when deploying NotPetya: weaponizing ransomware—a tool used, up until this point, only by criminal actors—developed to spread via a voracious viral worm in order to rapidly overtake civilian infrastructure.
A Shared PlayBook For Rogue States
So why should we care?
The alliance between North Korea and Russia provides a pretty grim proposal for the future of cyber and hybrid warfare. Besides the immediate ability to marshal assistance to Russia, I think there’s a more long-term danger to a meeting of these two doctrines. It’s my earnest opinion that unfettered cyberwarfare in such a fashion would be an understated development. It may prove as significant for international relations in this century as the arrival of nuclear weapons did in the previous one.
Both nations have effectively doubled-down on their isolation from much of the global community, and are embracing their roles as rogue states. To varying degrees, both have already shown a contempt for enforcing anything resembling an international norm in cyberspace. North Korea, with limited resources, has demonstrated how a highly skilled and state-backed cyber apparatus can serve as an asymmetric equalizer. By simply ignoring international norms, it’s generated billions to fund its nuclear ambitions while circumventing sanctions. For Russia, which faces increasing economic and geopolitical isolation, North Korea’s model may prove instructive.
Russia’s extensive resources, coupled with its ecosystem of cyber-criminals and hacktivists, give it the potential to adopt and expand on the DPRK’s tactics. Financially motivated and increasingly weaponized ransomware campaigns, global phishing networks, and the use of cyber operations for both intelligence and direct disruption could all scale dramatically under Russian adaptation.
As Russia refines its approach with insights from North Korea, the global community could face more sophisticated and persistent threats. The growing ties between these two pariah states should be a wake-up call: the playbook of rogue states is expanding, and so, too must the strategies to confront them.